What Best Describes the Security Threat of Spoofing
Q1 The following is a part of a threat model except _________. Drag the network attack technique on the left to the appropriate description or example on the right.
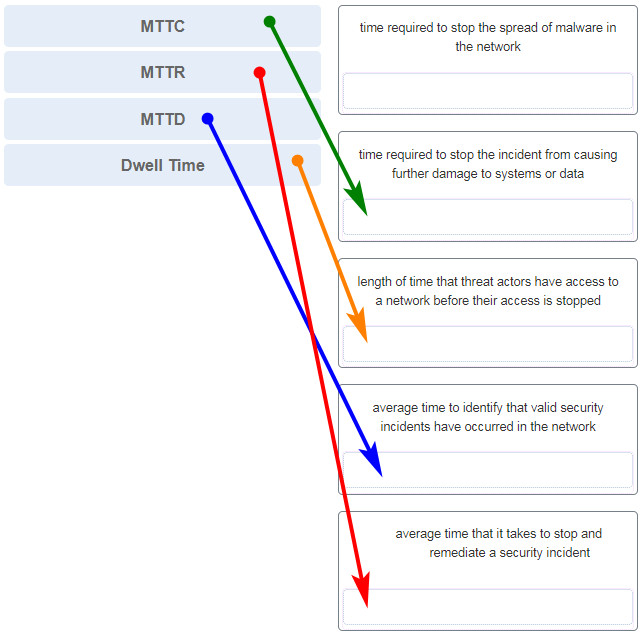
Cyberops Associate Version 1 0 Modules 1 2 Threat Actors And Defenders Group Exam
It is a fundamental concept in security that minimizes risk to the business or organization.

. A list of potential threats. The attack works as follows. What best describes the security threat of spoofing.
Intercepting traffic between two hosts or inserting false information into traffic between two hosts. What best describes the security threat of spoofing. Describe how ingress filtering can be used as a counter measure to safeguard against IP Spoofing and its level of effectiveness.
Perpetrators attempt to compromise or affect the operations of a system. What best describes the security threat of spoofing. Configuring the cell phone to act as a wireless access point means that the cell phone is now a rogue access point.
Sending bulk email to individuals lists or domains with the intention to prevent users from accessing email. Sending abnormally large amounts of data to a remote server to prevent user access to the server services. The employee unknowingly breached the security of the company network by allowing a user to access the network without connecting through the company access point.
Learn vocabulary terms and more with flashcards games and other study tools. The theft of intellectual property is a threat to information security. Which of the following best describes the threat modeling process.
Answers Explanation Hints. See answer 1 Best Answer. Q2 Which of the following security property does Spoofing violate.
Making data appear to come from a source that is not the actual source. What best describes the security threat of spoofing. Threat Modeling Interview Question-Answer.
Sending abnormally large amounts of data to a remote server to prevent user access to the server services. Successful attacks on organizations can lead to infected computer systems and networks data breaches andor loss of revenueall liable to affect the organizations public reputation. What best describes the security threat of spoofing.
We talked about this briefly during the authentication phase in an earlier module where one can generate fake bogus IP packets directly from an application. They scan the network to determine the IP addresses of at least two devices. Making data appear to come from a source that is not the actual source.
Asked Mar 17 2021 in Threat Modeling by sharadyadav1986. The attacker must have access to the network. There are two types of access control.
Start studying Spoofing Attacks. Domain 3 of the Security exam requires that you understand how to identify and minimize system threats to thwart would-be attackers and that you recognize the different types of assessment tools that are available to discover security threats and vulnerabilities. What best describes the security threat of spoofing.
Access control is a security technique that regulates who or what can view or use resources in a computing environment. Spoofing hampers which of the following Security foundations. So the following security threat talks about IP Spoofing.
What is ARP Spoofing ARP Poisoning An ARP spoofing also known as ARP poisoning is a Man in the Middle MitM attack that allows attackers to intercept communication between network devices. Sending bulk email to individuals lists or domains with the intention to prevent users from accessing email sending abnormally large amounts of data to a remote server to prevent user access to the server services intercepting traffic between. What best describes the security threat of spoofing.
Each technique may be used once more than once or not at all Drag. Cyber criminals utilize various tactics to spoof their identity ranging from spoofed email addresses websites or phone numbers to more advanced strategies like fraudulent IP addresses Domain Name Servers DNS or Address Resolution. Sending bulk email to individuals lists or domains with the intention to prevent users from accessing email sending abnormally large amounts of data to a remote server to prevent user access to the server services.
Select the best answer from below options a Fixed b Iterative. Sending bulk email to individuals lists or domains with the intention to prevent users from accessing email. Intercepting traffic between two hosts or inserting false information into traffic between two hosts.
Sending bulk email to individuals lists or domains with the intention to prevent users from accessing email. Q3 ________ generates a map that illustrates how the user moves through various features of the application. Spoofing is often the way a bad actor gains access in order to execute a larger cyber attack such as an advanced persistent threat or a man-in-the-middle attack.
What best describes the security threat of spoofing. Sending bulk email to individuals lists or domains with the intention to prevent users from accessing email. Spoofing occurs when a cyber criminal disguises themself as an individual business or entity to commit malicious acts.

7 Types Of Cyber Security Threats

Ccna Cyber Ops Chapter 6 Exam Answers Version 1 1 2019 Full 100

0 Response to "What Best Describes the Security Threat of Spoofing"
Post a Comment